KNOXVILLE, TN – A new, highly-effective phishing technique is targeting Gmail users, along with other email services.
Mark Maunder, the CEO of WordPress security plugin Wordfence, says the attacker will send an email to your Gmail account. That email may come from someone you know who has had their account hacked using this technique. It may also include something that looks like an image of an attachment you recognize from the sender.
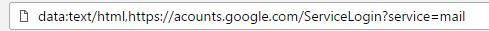
If you click on the image, expecting Gmail to give you a preview of the attachment, a new tab will open up, prompting you to sign in to your Gmail account again. At first glance, the location looks like a service login page, but it is actually a phishing attempt.
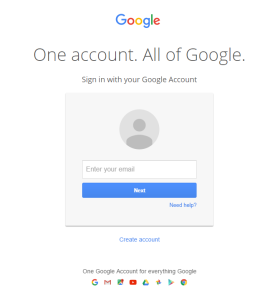
A sign-in page for Gmail pops-up. Once you complete sign-in, you account has been compromised. A commenter on Hacker News describes in clear terms what they experienced over the holiday break once they signed in to the fake page:
The attackers log in to your account immediately once they get the credentials, and they use one of your actual attachments, along with one of your actual subject lines, and send it to people in your contact list.
For example, they went into one student’s account, pulled an attachment with an athletic team practice schedule, generated the screenshot, and then paired that with a subject line that was tangentially related, and emailed it to the other members of the athletic team.”
“The attackers signing into your account happens very quickly. It may be automated or they may have a team standing by to process accounts as they are compromised,” said Maunder. “Once they have access to your account, the attacker also has full access to all your emails including sent and received at this point and may download the whole lot.”
How to protect yourself
To protect yourself from this phishing attack, you need to change what you are checking in the location bar.
Maunder said the phishing technique uses something called a ‘data URI.’ If you widen out the location bar it looks like this:
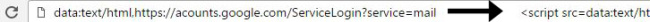
On the far right of the location browser, you can see the beginning of what is a very large chunk of text. This is actually a file that opens in a new tab and creates a completely functional fake Gmail login page which sends your credentials to the attacker.
When you sign in to any service, check the browser location bar and verify there isn’t any extra text. Also, consider using two-step authentication. You can find details on how to sign up for two-step authentication for Gmail here.
Check if your account has already been compromised
There is no sure way to check if your account has been compromised.
If in doubt, change your password immediately. Changing your password every few months is a good practice in general.
You can also check login activity on your Gmail account. Just open Gmail, click on Details (very small in the bottom right hand corner of your screen). This will show you all currently active sessions as well as your recent login history.
If you see active logins from unknown sources, you can force close them. If you see any logins in your history from places you don’t know, you may have been hacked.



